Searching “the biggest data breaches in the world” on Google and you will see the names mentioned there are all big brands, including leading technological brands like Facebook.
In today’s hyper-connected world, every business is at risk. In fact, a 2024 report by Check Point Research revealed that there has been an average of 1,876 cyberattacks per organization each week in Q3 2024, which represents a 75% increase compared to the same period in 2023.
One breach can mean lost revenue, a damaged reputation, and broken customer trust. With risks like these on the rise, strong website security isn’t just a nice-to-have - it’s absolutely essential.
That’s why being proactive is key. By following our website security best practices, you can protect sensitive information and maintain your brand’s credibility. Let us walk you through some effective strategies to help keep your site secure and your visitors protected.

The new reality of website security
Cyber threats don’t care about the size of your business or the industry you’re in. Every website, big or small, is a potential target. Hackers are constantly looking for vulnerabilities they can exploit - whether it’s to steal data, disrupt operations, or harm your reputation.
AI is rapidly reshaping the cyber threat landscape, which makes website security more challenging than ever. According to SoSafe’s 2025 Cybercrime Trends report, 87% of organizations encountered AI-powered cyberattacks in the past year. However, only 26% of those expressed high confidence in their ability to detect such attacks, underscoring a significant gap in cybersecurity readiness.
A stark example came in early 2024, when a Hong Kong company lost $25 million to a sophisticated deepfake scam. Scammers used AI to impersonate the company's CFO during a video call, tricking an employee into authorizing fraudulent fund transfers totaling HK$200 million across 15 transactions (Business Insider).
This new wave of cybercrime is not just more frequent - it’s more convincing and harder to spot security breaches. As AI advances, it's crucial for organizations to bolster their defenses to effectively detect and respond to these sophisticated threats.
Addressing AI-driven and emerging threats
1. The rise of AI-driven attacks
Traditional cybersecurity defenses were designed for a different era - one where threats were easier to spot and predict. Today, AI-powered attacks are changing the game. They move quickly, adapt on the fly, and easily slip past old-school security tools. Here’s a look at how AI is helping attackers stay one step ahead.
- Dynamic evasion: AI constantly changes malware patterns, making them hard for conventional defenses to recognize.
- Smarter phishing: AI creates highly personalized phishing attacks that bypass basic filters.
- Rapid vulnerability exploitation: AI quickly identifies and exploits security flaws before defenses can respond.
- Bypassing static controls: AI adapts and learns from failed attacks to find new ways around traditional security.
- Mimicking legitimate behavior: AI-driven threats imitate normal user actions, complicating detection efforts.
How can businesses keep up?
The answer lies in smart partnerships and proactive tools. Solutions like Cloudflare or Datadome use advanced anomaly detection and AI to spot suspicious behavior before it becomes a breach. These platforms are designed to evolve alongside emerging threats, providing your business with the protection it needs without the complexity of building it in-house.
2. Third-party and supply chain vulnerabilities
Relying on external components such as third-party scripts, plugins, and APIs can streamline development and add functionality, but they also introduce hidden risks.
|
Element |
Definition |
Risk |
Impact |
|
Third-party scripts |
External JavaScript files embedded from other domains (e.g., analytics, ads, chat widgets) |
|
Unauthorized script changes can comprise user data or inject malicious code into your site. |
|
Plugins (CMS extensions, add-ons) |
Software modules installed to add features to CMS platforms like WordPress, Joomla, etc. |
|
A single compromised plugin can lead to full-site takeovers, data breaches, or malware distribution. |
|
APIs (Application programming interfaces) |
Interfaces that allow your site to communicate with external systems (e.g., payment processors, shipping services). |
|
Vulnerable APIs can lead to data leaks, service disruptions, or unauthorized access to backend systems. |
How to address? Get to know Open Worldwide Application Security Project (OWASP)
OWASP, short for the Open Worldwide Application Security Project, is a nonprofit foundation dedicated to the improvement of software security. Known for its widely used resources like the OWASP Top 10, it offers practical, community-driven tools and guidance to make secure development more accessible to everyone.
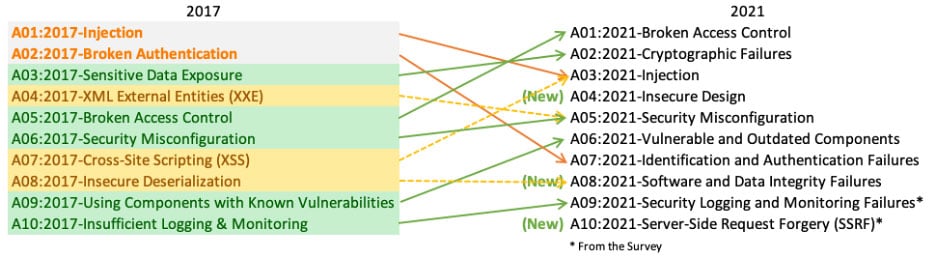
Latest OWASP update: Top 10 web application security risks for 2021. Source: owasp.org
Website security best practices for all sites
Keeping your website safe is more important than ever. Let’s follow these key security practices and protect you and your visitors from cyber threats.
- Think security-first from the start: Security shouldn’t be an afterthought. Bake it into your website design and development process from day one. This includes planning for data protection, secure architecture, and access controls before a single line of code is written.
- Run a security audit: Processing such an audit helps you spot vulnerabilities and ensure your site meets essential protection standards. Niteco’s Performance Insights includes built-in security checks that highlight key risk areas unique to your site. Start your free audit now!
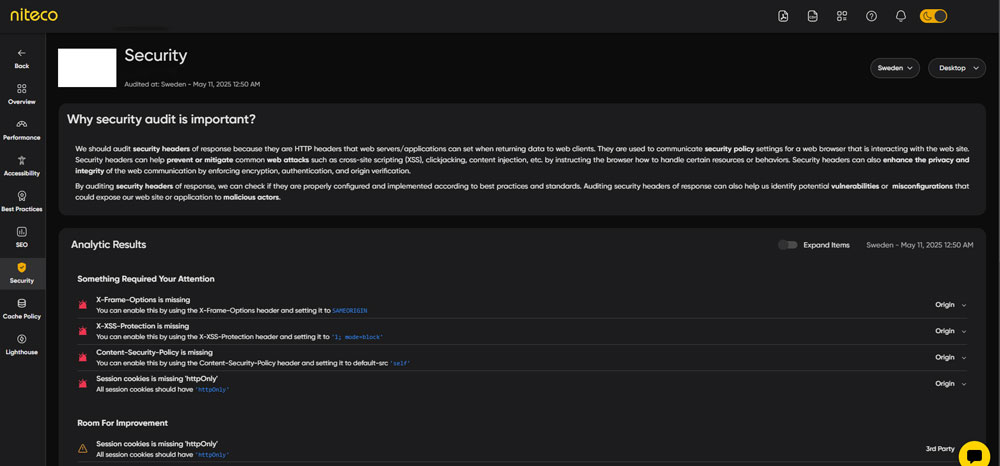
- Respect regional data privacy standards: It’s crucial to ensure that data protection measures align with local regulations. Privacy laws differ by region - for instance, GDPR emphasizes user consent and data rights, while China’s PIPL imposes strict controls on data localization. This approach not only reduces legal risk but also strengthens trust with users in different markets.
- Choose secure hosting and domain services: Select a trustworthy hosting provider that offers robust security features such as firewalls, automatic backups, and regular security scanning. Ensure your domain services are also well-protected to prevent domain hijacking.
- Enable HTTPS with SSL/TLS encryption: HTTPS is a must-have security feature today. It encrypts all data transferred between your website and its users, keeping sensitive info like passwords and payment details safe from prying eyes.
- Implement strong authentication and access control: Passwords should be strong and unique - no “password123” here! Adding multi-factor authentication (MFA) adds an extra layer of defense by requiring a second confirmation step. Limit user access based on roles to reduce the risk if an account is compromised.
- Keep your website and software updated: Hackers love outdated software because it often has known vulnerabilities. Regularly update your CMS, plugins, themes, and server software to patch security holes. Staying up-to-date is one of the simplest yet most effective ways to keep your site secure.
If you’re at the old version of .NET or Optimizely CMS/Commerce, it’s time to make the smart and save move. Upgrade to the latest version of Optimizely with stronger security.
How to prevent website data breaches
Data breaches often stem from security vulnerabilities and can happen to any site. However, the right measures in place will answer the question on how to secure website against the risk. Here’s how to get started.
- Defense-in-depth: Effective cybersecurity relies on multiple, overlapping controls that work synergistically to provide comprehensive protection, detecting, preventing, and mitigating attacks at various stages.
- Deploy Web Application Firewalls (WAFs) and malware scanners: Install a WAF to filter and block malicious traffic before it reaches your site. Combine this with regular malware scans to detect and remove threats like viruses, trojans, or backdoors that could compromise your data.
- Run regular vulnerability scans and security audits: Schedule routine vulnerability scans to catch outdated software, misconfigurations, and other weaknesses. Pair this with periodic security audits to assess your overall posture and confirm best practices are being implemented.
- Back up your site regularly and test recovery: Create automated, regular backups of your website’s files and databases, and store them securely offline or in isolated environments. Just as important-regularly test your recovery process so you’re ready if disaster strikes.
- Limit user access with least-privilege policies: Set user permissions based on what’s necessary for each role. Only grant administrative access when truly needed, and regularly review accounts to remove or adjust unused or outdated permissions.
Sector-specific security imperatives
Commerce platforms: Protecting financial transactions
Commerce sites are prime targets for cybercriminals due to the wealth of sensitive customer data they store, such as credit card information, personal addresses, and purchase histories. This financial and personal data is highly valuable and can be exploited for fraud, identity theft, or targeted phishing attacks. As a result, these sites can experience financial losses, regulatory penalties, and damage to customer trust.
Common threats
- Phishing: Attackers trick users into revealing sensitive information (login credentials, financial information, or personal details) through deceptive emails or websites.
- SQL injection: Malicious users exploit vulnerabilities in the website's code by inserting harmful SQL code, allowing them to steal or manipulate data.
- Credential-stuffing: Cybercriminals use stolen username and password combinations to gain unauthorized access to multiple accounts.
- Fraudulent transactions: Criminals use stolen credit card or other payment methods to purchase goods from your business before the transactions get noticed and reversed, leaving you with the bill.
Best security practices
- PCI DSS compliance: Make sure your website adheres to the Payment Card Industry Data Security Standard (PCI DSS). This set of security requirements is specifically designed to protect cardholder information and mitigate fraud. Being compliant not only enhances website security but also fosters customer trust by showcasing your commitment to data protection.
- Transaction encryption: Use SSL/TLS encryption to secure the transmission of sensitive information, like credit card numbers and personal details, between customers and your website. This encryption safeguards data from interception by unauthorized parties during the checkout process.
- Patch vulnerabilities: Keep your software components up to date by regularly applying patches and updates. Unpatched vulnerabilities can be an easy entry point for attackers to exploit, so it's essential to stay current with security fixes released by software vendors.
- Offload sensitive data: Consider using third-party providers with a well-established track record for storing sensitive data. For example, OneTrust for user logins (passwords) and Stripe for card information. Only store the minimum level of sensitive data your organization should be responsible for.
- Automatic payment monitoring: Use a payment provider that can automatically identify suspicious transactions, then make sure your website does not automatically process orders attached to suspicious transactions without human review.
Healthcare portals: Securing sensitive patient data
Healthcare websites and patient portals manage a wide range of highly sensitive data-ranging from medical records and insurance details to Social Security numbers. Because of the critical nature of this information, these platforms are frequent targets for cyber threats.
Key threat: Ransomware attacks
Hospitals and healthcare providers are increasingly targeted by ransomware. These attacks can lock hospitals out of their own systems, halting operations and delaying patient treatment until a ransom is paid.
Best security practices
- Multi-Factor Authentication (MFA): Implementing MFA to electronic health records (EHRs) to add an extra layer of security beyond passwords. This reduces the risk of unauthorized entry even if credentials are stolen.
- Network segmentation: Divide the network into separate zones (e.g., separating administrative systems from medical equipment or patient portals) to limit the spread of malware and keep core systems protected if a breach occurs.
- Encrypted backups: Regularly back up patient data using strong encryption methods and store it securely-ideally offline. Encrypted backups ensure that data remains safe and recoverable in the event of ransomware or other destructive attacks.
- Vendor security audits: Conduct thorough and regular audits of third-party vendors to ensure they follow stringent security protocols and do not introduce vulnerabilities into your system.
Educational institutions: Protecting academic and research systems
Universities, colleges, and online learning platforms store extensive databases containing sensitive information-student records, academic research, financial data, and intellectual property. This makes them attractive targets for cybercriminals.
Key threats
- Decentralized IT systems: Many educational institutions operate with independently managed departments and networks, which complicates the enforcement of uniform security policies. This fragmentation can lead to gaps in protection.
- Social engineering attacks: Attackers often take advantage of human behavior through phishing emails or deceptive messages that trick students, faculty, or staff into disclosing login credentials or downloading malicious files.
Best security practices
- Role-based access controls: Ensure that individuals have access only to the information necessary for their responsibilities. This minimizes the risk of data leaks and unauthorized activity.
- Cybersecurity training: Regularly provide awareness programs for students, faculty, and staff to recognize phishing attempts, avoid unsafe online behavior, and get the basics of how to prevent security breaches. Education is a key defense against social engineering.
- Patching outdated systems: Keep all systems - such as servers, learning management platforms, and devices - up to date with the latest security patches. Outdated software often serves as an easy entry point for attackers.
Government and public service websites: Defending critical infrastructure
Government and public service websites-such as tax processing, voting systems, and public records-are vital components of national infrastructure. Due to the sensitive nature of the data and their importance to public welfare, these sites are high-value targets for sophisticated state-sponsored cyberattacks.
Key threats
- Municipal website attacks: Local government websites are often under-resourced and more susceptible to attack. Cybercriminals frequently exploit unsecured APIs and outdated systems to gain access or disrupt services.
- State-sponsored attacks: Nation-state actors may target public platforms to acquire sensitive data, spread misinformation, or interfere with government functions-particularly around elections or tax season.
Best security practices
- Zero-trust frameworks: Embrace a zero-trust security approach that requires continuous verification of every user and device attempting to access government systems, regardless of their location within the network.
- DDoS protection: Establish robust defenses against Distributed Denial-of-Service (DDoS) attacks, which can overwhelm servers and bring down public-facing websites. Cloud-based DDoS mitigation services can absorb and deflect large-scale attacks.
- Offline immutable backups: Maintain regular, offline backups that cannot be altered or deleted (immutable). In the event of ransomware or data loss, these backups ensure recovery without paying a ransom or relying on compromised systems.
Building a culture of security and readiness (Long-term mindset)
Building a strong security culture starts with people. Regular training for employees and administrators helps promote good security habits and reduces the risk of human error.
Transparent communication with users builds trust. Letting users know what security measures are in place-and how they can protect their own accounts-encourages safer behavior across the board.
Finally, preparation is key. It's good practice to maintain an up-to-date security checklist and incident response plan. This ensures your team is ready to act quickly and effectively when security issues arise.
Conclusion
Website security is a long-term commitment, not a one-time task. Key actions like secure hosting, HTTPS, strong authentication, regular updates, and reliable backups form the foundation. It's also important to scan for vulnerabilities, limit user access, and train staff in cybersecurity basics.
Different websites face different risks so knowing your site’s specific threats helps you apply the right defenses.
In the end, strong security protects more than just data-it builds user trust and supports the long-term success of your business. At Niteco, we are here to help you take the next step toward enhancing your security and guaranteeing your business, so feel free to get in touch.



